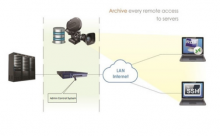
HARD DISK RECOVERY KEY FEATURES The admin control system is a product that has been developed to create a firewall for the application layer as well as event logging of all the details of the remote access protocols. By using such a product, it is possible to view and check all the communication details established through the RDP and SSH protocols in the video format. In addition, the management console provides the ability to search specific expressions, special events, etc. in videos as well as typed parameters and commands by users. This system can be completely transparent in the organization’s network, in which case no changes will be made to network settings, servers, clients or how users are used. Of course, depending on the user’s preferences, it is also possible to use this product as non-transparent. The system includes a hardware server or a virtual machine. In order to provide the services mentioned, this system needs to be placed in the middle of connecting users to the relevant servers. MAIN FEATURES ● Transparent functionality and no need for changes to the server, clients and application - Lack of users awareness of the existence of the system - Simplicity and no need for special training ● Simplicity and transparency in the process of installing the system and no need for changes in network configuration ● Ability to use the system in a non-transparent system on the network using Port Forwarding ● Usable for devices on which it is not possible to install Agent (such as switches, routers etc.) ● Monitoring the web mails: Gmail, Yahoo mail TECHNICAL SPECIFICATION ● Ability to view and monitor online ● Live monitoring of user activity in RDP and SSH communications ● Supports SSH protocol ● Searches features in entered commands ● Copies files and information exchanged between users and servers ● Ability to define users and control remote access to various network resources ● Ability to restrict users on a specific computer or address range ● Ability to authenticate users locally or through directory servers such as active directory ● Encrypts recorded files to achieve undeniability and prevents content changes features ● Port forwarding support
| Attachment | Size |
|---|---|
| chapter 6-11(40)_299.pdf | 208.74 KB |